| Table of Contents |
|---|
Introduction
| English |
|---|
The Sync LDAP User Directory Manager is a hybrid solution that allows you to make use of the user objects from your organization's LDAP server and maintaining organization structure (organization / department / group) locally inside Joget. This plugin allows you to import user objects from LDAP server on demand into Joget built in user directory manager to reduce its dependency on the LDAP server for improved performance. The primary benefit for using Sync LDAP is better performance for user-data related processing
The built in user directory manager is still the primary handler when this plugin is activated. Once you have synchronized the users to the local directory manager, you can assign the users to your organization/department/group/grade which created locally. With the use of this plugin, we will be able to reduce the conventional load and dependency on the LDAP server and to only use it for authentication purpose. A new feature added in Joget DX is the "Auto schedule sync" property. The Joget admin can also click on the Sync Users button to manually perform an LDAP sync. Joget identifies users on Sync LDAP if the password column in database is "(NULL)", which causes the following to take place: |
- Users cannot edit their profile.
- Admin cannot use @"Admin Bar > Users > Setup User"@ to edit user information.
- Only records with password equal NULL will sync to your LDAP directory.
If the user wants to change his password, recommended is to change it in LDAP/AD.
- If there's a new user in LDAP, it will be created in Joget user database. If a user from LDAP does not exist anymore in LDAP but exists in Joget, then the user will get disabled/inactive in Joget, and it will never be deleted.
- If LDAP user is deleted from AD, it will not delete the record in dir_user
- Upon sync, related local user record will be set to inactive
- If local user record is deleted instead but still exist in AD, it will just be re-imported again upon next sync
Sync LDAP Properties
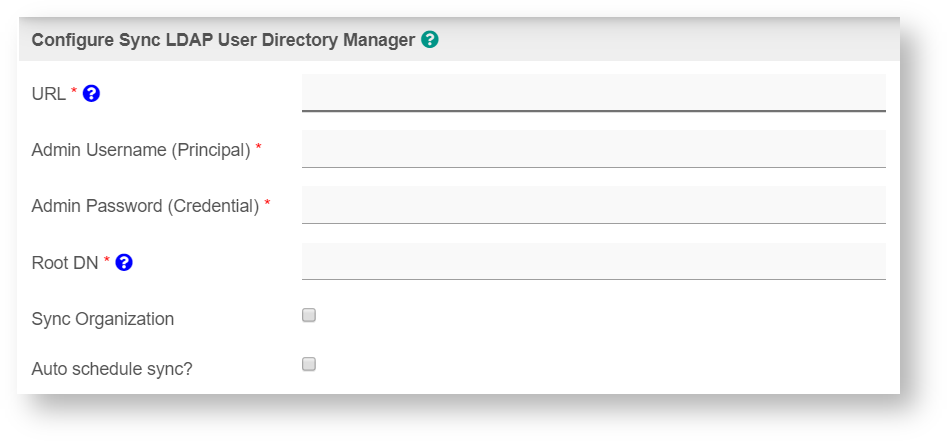
Configuring Sync LDAP
Figure 1: Configure Sync LDAP
Figure 2: Sync Organization Enabled
| Name | Description / Sample Value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| URL | ||||||||||
Admin Username (Principal) | cn=admin,dc=joget,dc=org | |||||||||
Admin Password (Credential) | Input the admin password for your LDAP/AD. | |||||||||
| Root DN | Set the root DB, for example "eg. DC=Joget,DC=org". | |||||||||
Sync Organization| Panel | | |||||||||
| Perform synchronization not just to user objects, but to the whole organizational structure including Group, Department, Grade as well. By enabling this feature, you will need to configure the following as well.
Please refer to documentation for setting up Group, Department, and Grade in LDAP Directory Manager. | Auto schedule sync? |
| |||||||
| Auto schedule sync? | Clicking this checkbox to automatically sync your LDAP on a schedule, will display additional options as follows:
|
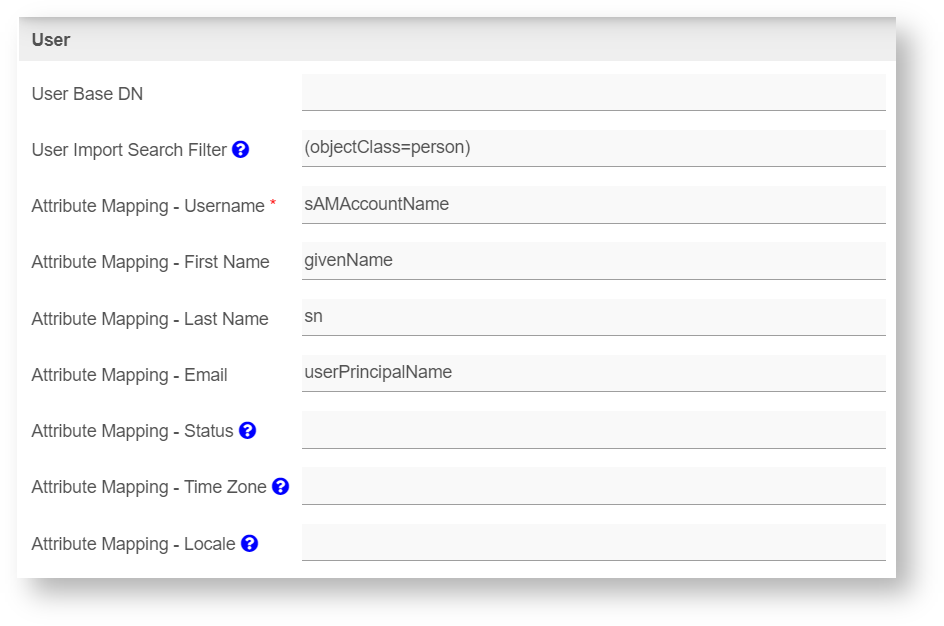
User
Figure 2: User Properties
| Name | Description / Sample Value | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| User Base DN | Set the user base DN property.
| |||||||||||||||
| User Import Search Filter | (objectClass=person)
More details at LDAP Directory Manager#ConfiguringTheUserImportSearchFilter. | |||||||||||||||
Attribute Mapping - Username | cn | |||||||||||||||
Attribute Mapping - First Name | givenName | |||||||||||||||
Attribute Mapping - Last Name | sn | |||||||||||||||
Attribute Mapping - Email | ||||||||||||||||
Attribute Mapping - Status | status | |||||||||||||||
Attribute Mapping - Time Zone | 8 | |||||||||||||||
Attribute Mapping - Locale | en_US |
Employment
Figure 3: Employment Properties
| Name | Description / Sample Value |
|---|---|
| Attribute Mapping - Employee Code | employeeCode |
| Attribute Mapping - Job Title | jobTitle |
| Attribute Mapping - Report To | Use this if an LDAP user that a user reports to is kept in LDAP user entry. eg. manager |
| Map To "Report To" Entry Attribute | Used together with "Attribute Mapping - Report To". eg. distinguishedName |
| Attribute Mapping - Metas | Additional attributes to retrieve using #user.USERNAME.meta.KEY# or #currentUser.meta.KEY# |
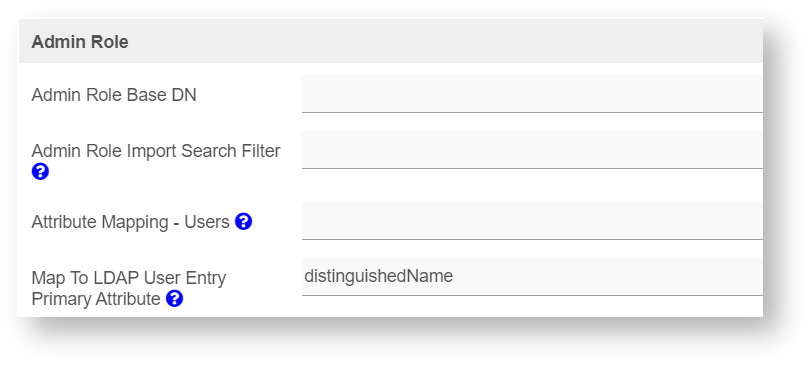
Admin Role
Figure 4: Admin Role Properties
| Name | Description / Sample Value |
|---|---|
| Admin Role Base DN | Set the Admin Role Base DN |
| Admin Role Import Search Filter | eg. (objectClass=group) |
| Attribute Mapping - Users | Use this if the admin role of user(s) is kept in LDAP entry. eg. member |
| Map To LDAP User Entry Primary Attribute | Map To LDAP User Entry Primary Attribute |
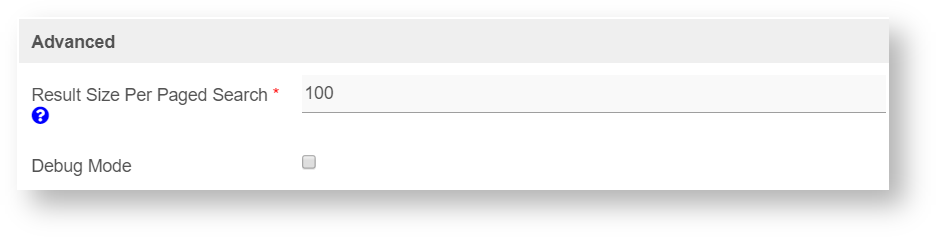
Advance
Figure 5: Advance Properties
...
Related Documentation
Security Enhanced Directory Manager
...